lm2ntcrack : NT Hash cracker from LM Password
This website allows you to decrypt, if you're lucky, your ntlm hashes, and give you the corresponding plaintext. We proceed by comparing your hash with our online database, which contains more than 1.000.000.000 different hashes. OnlineHashCrack is a powerful hash cracking and recovery online service for MD5 NTLM Wordpress Joomla SHA1 MySQL OSX WPA, PMKID, Office Docs, Archives, PDF, iTunes and more! Cracking Windows Password Hashes with Metasploit and John The output of metasploit’s ‘hashdump’ can be fed directly to John to crack with format ‘nt’ or ‘nt2’. Let assume a running meterpreter session, by gaining system privileges then issuing ‘hashdump’ we can obtain a copy of all password hashes on the system: 1. Cracking the majority of such passwords normally takes just a few minutes. The NT hash is free from the disadvantages, common to the LM hash. Consequently, it is much harder to pick the right password to a known NT hash than to an LM hash. Hashes.com este un serviciu de cautare hashuri. Acesta iti permite sa introduci un hash MD5, SHA-1, Vbulletin, Invision Power Board, MyBB, Bcrypt, Wordpress, SHA-256, SHA-512, MYSQL5, etc si sa-i cauti (gasesti) rezolvarea corespunzatoare in baza noastra de hashuri deja rezolvate.
lm2ntcrack provides a simple way to crack instantly Microsoft Windows NT Hash (MD4) when the LM Password is known. lm2ntcrack is Free and Open Source software.
This software is entirely written in Perl, so its easily ported and installed.
Pen-testers often encounter a problem during Windows penetration testing and password assessment.
Dumping Windows passwords hashes, permits to crack many LM passwords but cracked password cannot be used as is (uppercase version of the Windows password).
On the other hand, password cracking on NT hash is long and after few days it cracks only some password.
So you’ve got the LM password but it is only in UpperCase because LM Hashes are not case sensitive. So, these passwords cannot be reuse in this form.
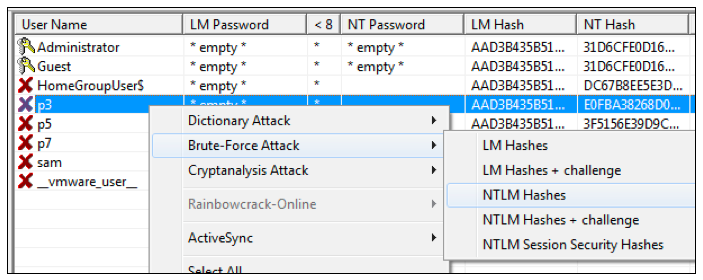
Example : Password cracker output for “Administrator” account
* LM password is ADMINISTRAT0R.
* NT password is ?????????????.
I’m not so lucky because the case-sensitive password isn’t “administrat0r” or “Administrat0r”. So I cannot use this to connect on the audited Windows system.
This password contains 13 characters but launching my password cracker on the NT hash is a waste of time and there is a poor chance of success.
Note :
* Password length : 13 characters.
* Details : 1 number + 12 case-sensitives letters.
* Possibilities : 2^12 = 4096 choices. (Cannot test them all manually)

Nt Hash Tables
Nt Hash Decrypter
In this example, lm2ntcrack will generate the 4096 possibilities for the password ADMINISTRAT0R and, for each one, the associated NT MD4 hash. Then, search for matching with the dumped hash.
Nt Hash Converter Online
Execution time : < 2 seconds to crack more than 1200 NT Hashes To read more about this and download the script visit http://www.xmcopartners.com/lm2ntcrack/index.html